Researchers have discovered over two dozen Python packages on the PyPI registry that are pushing info-stealing malware. [...]
...moreSummary
Total Articles Found: 21
Top sources:
Top Keywords:
- Security: 20
- Technology: 3
- Hardware: 1
Top Authors
- Ax Sharma: 21
Top Articles:
- An encrypted ZIP file can have two correct passwords — here's why
- Log4j 2.17.1 out now, fixes new remote code execution bug
- Python also impacted by critical IP address validation vulnerability
- 35,000 code repos not hacked—but clones flood GitHub to serve malware
- Codecov hackers gained access to Monday.com source code
- HashiCorp is the latest victim of Codecov supply-chain attack
- Software maker removes "backdoor" giving root access to radio devices
- PyPI package 'keep' mistakenly included a password stealer
- Tutanota encrypted email service suffers DDoS cyberattacks
- Malicious PyPI packages with over 10,000 downloads taken down
Dozens of PyPI packages caught dropping 'W4SP' info-stealing malware
This image shows its own MD5 checksum — and it's kind of a big deal
Generating checksums—cryptographic hashes such as MD5 or SHA-256 functions for files is hardly anything new and one of the most efficient means to ascertain the integrity of a file, or to check if two files are identical. But a researcher has generated an image that visibly contains its own MD5 hash. [...]
...moreThis image contains its own MD5 checksum — and it's kind of a big deal
Generating checksums—cryptographic hashes such as MD5 or SHA-256 functions for files is hardly anything new and one of the most efficient means to ascertain the integrity of a file, or to check if two files are identical. But a researcher has generated an image that visibly contains its own MD5 hash. [...]
...moreAn encrypted ZIP file can have two correct passwords — here's why
Password-protected ZIP archives are common means of compressing and sharing sets of files—from sensitive documents to malware samples to even malware (phishing "invoices" in emails). But, did you know it is possible for an encrypted ZIP file to have two correct passwords, with both producing the same outcome on extraction? [...]
...more35,000 code repos not hacked—but clones flood GitHub to serve malware
Thousands of GitHub repositories were cloned and altered to include malware, a software engineer discovered. [...]
...morePyPI package 'keep' mistakenly included a password stealer
PyPI packages 'keep,' 'pyanxdns,' 'api-res-py' were found to contain a password-stealer and a backdoor due to the presence of malicious 'request' dependency within some versions. [...]
...moreHeroku admits that customer credentials were stolen in cyberattack
Heroku has now revealed that the stolen GitHub integration OAuth tokens from last month further led to the compromise of an internal customer database. The Salesforce-owned cloud platform acknowledged the same compromised token was used by attackers to exfiltrate customers' hashed and salted passwords from "a database." [...]
...moreTwitter account of FBI's fake chat app, ANOM seen trolling today
The Twitter account previously associated with the ANOM chat app is posting frivolous tweets this week. ANOM was a fake encrypted messaging platform created as part of a global sting operation led by the U.S. FBI, Australian Federal Police (AFP), and other law enforcement agencies to catch criminals. [...]
...moreLog4j 2.17.1 out now, fixes new remote code execution bug
Apache has released another Log4j version, 2.17.1 fixing a newly discovered remote code execution (RCE) vulnerability in 2.17.0, tracked as CVE-2021-44832. Prior to today, 2.17.0 was the most recent version of Log4j and deemed the safest release to upgrade to, but that advice has now evolved. [...]
...moreMalicious PyPI packages with over 10,000 downloads taken down
The Python Package Index (PyPI) registry has removed three malicious Python packages aimed at exfiltrating environment variables and dropping trojans on the infected machines. These malicious packages are estimated to have generated over 10,000 downloads and mirrors put together, according to the researchers' report. [...]
...moreAtlassian Trello is down — second outage this week
Trello is down for many users around the world, second time this week. Trello is a web-based TODO list-style platform owned by Atlassian, makers of Jira and Confluence. [...]
...moreSoftware maker removes "backdoor" giving root access to radio devices
The author of a popular software-defined radio (SDR) project has removed a "backdoor" from radio devices that granted root-level access. The backdoor had been, according to the author, present in all versions of KiwiSDR devices for the purposes of remote administration and debugging. [...]
...moreMozilla Firefox to roll out DNS over HTTPS for Canadian users
Mozilla has decided to roll out the DNS over HTTPS (DoH) feature by default for Canadian Firefox users later this month. The move comes after DoH has already been offered to US-based Firefox users since 2020. [...]
...moreOnlyFans, Twitter ban users for leaking politician's BDSM video
This week, Twitter and OnlyFans have banned user accounts that illicitly leaked a BSDM video featuring a New York City city council candidate. As reported by Motherboard, the video of 26-year old Zack Weiner began circulating on Twitter and OnlyFans via accounts with identical usernames and profile pictures. [...]
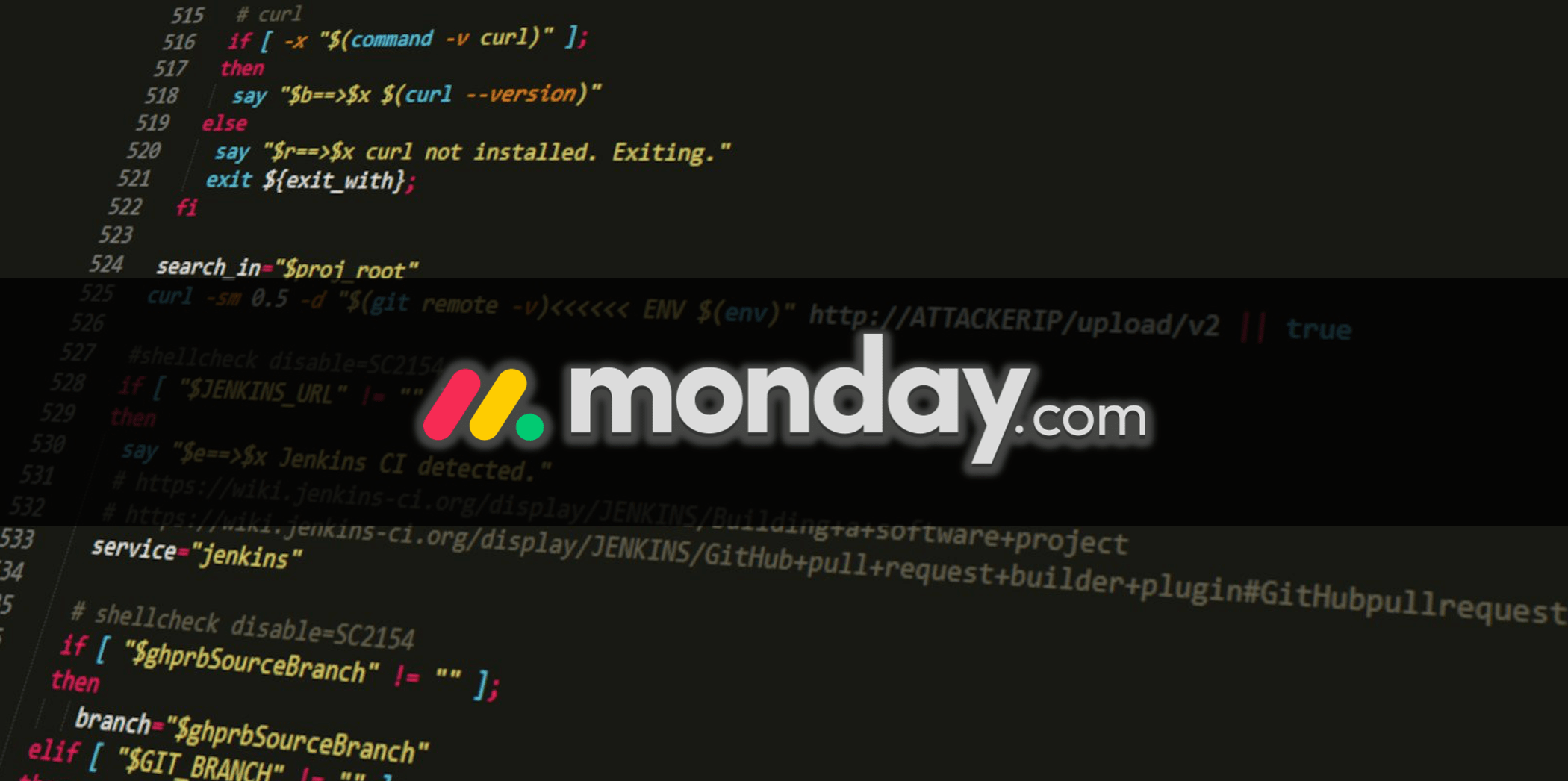
...moreCodecov hackers gained access to Monday.com source code
Monday.com has recently disclosed the impact of the Codecov supply-chain attack that affected multiple companies. As reported by BleepingComputer last month, popular code coverage tool Codecov had been a victim of a supply-chain attack that lasted for two months. [...]
...morePython also impacted by critical IP address validation vulnerability
Python 3.3 standard library 'ipaddress' suffers from a critical IP address vulnerability (CVE-2021-29921) identical to the flaw that was reported in the "netmask" library earlier this year. [...]
...moreHashiCorp is the latest victim of Codecov supply-chain attack
Open-source software tools and Vault maker HashiCorp has disclosed a security incident that occurred due to the recent Codecov attack. HashiCorp, a Codecov customer, has stated that the recent Codecov supply-chain attack aimed at collecting developer credentials led to the exposure of HashiCorp's GPG signing key. [...]
...moreGitHub Actions being actively abused to mine cryptocurrency on GitHub servers
GitHub Actions has been abused by attackers to mine cryptocurrency using GitHub's servers, automatically.The particular attack adds malicious GitHub Actions code to repositories forked from legitimate ones, and further creates a Pull Request for the original repository maintainers to merge the code back, to alter the original code. [...]
...moreTutanota encrypted email service suffers DDoS cyberattacks
Encrypted email service, Tutanota has experienced a series of DDoS attacks this week, first targeting the Tutanota website and further its DNS providers. [...]
...moreD-Link blunder: Firmware encryption key exposed in unencrypted image

Published: 2020-07-22 16:01:01
Popularity: 41
Author: Ax Sharma
Keywords:
The router manufacturer leaks encryption keys in some firmware versions letting reverse engineers decrypt the latest firmware images. [...]
...moreGitHub projects targeted with malicious commits to frame researcher
🤖: ""Git hacked""
GitHub projects have been targeted with malicious commits and pull requests, in an attempt to inject backdoors into these projects. Most recently, the GitHub repository of Exo Labs, an AI and machine learning startup, was targeted in the attack, which has left many wondering about the attacker's true intentions. [...]
...more









.jpg)


